Unfortunately, the story usually goes “we got infected with ransomware, it was only when we got in on Monday that we realised, and by then it was too late.” Most organisations are aware of the importance of good cyber security practices, but many are still underprepared for the “when and not if”. Keeping a constant eye on what is taking place on your network is the best way to contain an attack.
Ransomware damage costs will rise to $11.5 billion in 2019 and a business will fall victim to a ransomware attack every 14 seconds at that time.
82% of employers report a shortage of cybersecurity skills.
(ISSA)
With technology available to capture logs and give you real time alerts when there is potentially malicious activity on your network, the task for identifying and then containing a breach seems simple. The reality, in fact, is that skilled resource is scarce and hard to retain, and time is of the essence when it comes to reacting to an attack. GDPR requires breaches to be fully reported within 72 hours.
The top 6 business challenges we see
- Not enough time or capability to respond using existing IT resource
- Difficult to convert business need into the right technical scope
- Understanding what is needed, on a technical level
- The spiraling volume and complexity of attacks is increasing the average dwell time of an attacker, increasing risks further
- Difficulty in securing budget for managed security services
- Justifying the ROI of security services
The top 6 questions we get asked
- Can you detect threats on a 247x365 basis?
- How quickly will you respond?
- What certifications do you carry?
- Can you help me with my PCI compliance?
- Will you be able to cover my hybrid network
- How do you differentiate from the competition?
Right-sizing the scope is critical
Networks are complex and the volume of data is enormous so identifying what should and should not be in scope for centralised log collection and analysis can be difficult. Often, installations are either over-scoped, increasing cost and complexity or under-scoped increasing the potential for an attack to go undetected. With limited understanding of how attacks evolve and which systems to collect data, tailoring the right solution can be a painful, time-consuming, and costly exercise.
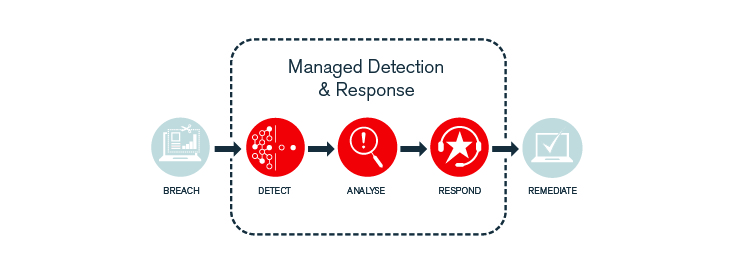
MTTD and MTTR are critical KPIs
Managed Detection and Response services supplement your team with skilled security professionals whose only task is to spot the potential for an attack and contain in the shortest time possible. Outsourcing detection and response provides immediate value:
- Extended security team capable of Threat Hunting, Vulnerability Analysis, Attack Investigation and Response
- 247x365 alerting to potential attacks
- 15 minute SLAs for critical issues
- Established processes and technology stack to reduce the time to value
- Mean time to detection (MTTD) and Mean time to respond (MTTR) reduced to hours rather than months or years
Our customers’ drivers for managed security services
Regulations and Compliance
- PCI DSS mandates the collection and human analysis of logs for malicious activity
- ICO and GDPR fines are now so significant that investing is cheaper than the fine
- FCA, NHS, LocalGov all have standards that recommend or mandate that log aggregation and analysis is embedded in the security strategy
- GDPR requires breaches to be fully reported within 72 hours
Brand, reputation and revenue protection
- Implementation of a Managed Detection and Response (MDR) service is a requirement to assure revenues from existing customer relationships or to access specific markets e.g. SaaS providers
- Breach prevention is a protection of the reputation and brand of an organisation. The average share price drops by 8% for example (link)
- Reduce the cost of the breach. Most breaches are the result of nuisance attackers or collateral damage from indiscriminate attacks. Some though, are “acts of war” as in the case of NotPetya. The costs for DLA Piper ran into millions of pounds but because the attack was launched by the Russian Government, UK insurers deemed it an “act of war” and therefore refused to pay for the losses (DLA Piper denied insurance)
- 2019 Verizon Data Breach study, nation state attacks have increased from 12 percent of attacks in 2017 to 23 percent in 2018. In house detection is the first line in the insurance strategy
Call to discuss your requirements with our security consultants
Get an accurate solution design, contextual with your unique business challenges.
Book a Proof of Concept or an Initial Needs Analysis assessment
If you are not sure what you need or are building a business case for Managed Detection and Response services, it is essential that the needs analysis is thorough. We will map out your environment including people, processes and technology enabling you to specify the right solution.
Claranet network, security and cloud credentials
- 20+ years in cybersecurity
- 3 SOCs across UK, Portugal and France
- Founding member of CREST
- CREST Certified SOC provider
- 70+ cybersecurity experts
- References and experience across all verticals
- One of 5 companies globally to carry AWS, Azure, and GCP accreditation









