Windows Autopatch - Automated update management for companies

Timothy Borchert
Senior Workplace Consultant
The same game over and over again - Patch Tuesday, Office updates, Edge updates. Only Teams runs by itself. Windows Autopatch brings order to this update carousel by centralising all important update functions - integrated and reliable. In this article, you will find out how Windows Autopatch works, what advantages it offers and how you can plan your start. You will see how routine tasks can be automated, risks are reduced and your IT is noticeably relieved - with familiar tools such as Microsoft Intune.
The challenges of modern Windows update management
Many companies still manage Windows patches with traditional tools such as Windows Server Update Services (WSUS) or rely on Microsoft Intune or Windows Update for Business (WUfB), but often in isolation and without a coordinated strategy. This creates a complex web of patchdays, Group Policies (GPO), Mobile Device Management (MDM) and security requirements that is difficult to manage.
IT teams are under pressure: on the one hand, they have to regularly update devices to close security gaps, while on the other, they have to ensure ongoing operations. There is often a lack of time, personnel and clear processes. Update distribution is often still done manually. However, manual processes are prone to errors, guidelines sometimes contradict each other and updates are repeatedly delayed. The tools used often offer many options, but without a clear structure, Windows update management quickly becomes a permanent construction site.
Ambitious IT decision-makers are looking for a way to master this complexity. They want a solution that automates, reduces the workload and integrates into existing device management. This is exactly where Windows Autopatch comes in.
What is Windows Autopatch?
Windows Autopatch is a cloud-based service within Microsoft Intune that should not be confused with Windows Autopilot. While Autopilot provides and configures devices, Windows Autopatch takes over their ongoing supply of updates. It automates the distribution of Windows Feature Updates, Windows Security Updates, Office Updates and Microsoft Edge Updates - customised to the respective environment and without manual intervention.
Architecture & Deployment Rings
The architecture of Windows Autopatch is based on close integration with Intune, Windows Update for Business and Microsoft Entra ID. Devices are automatically categorised into so-called deployment rings, i.e. device groups that receive updates in stages. Technically, these rings are mapped by update rings and Entra groups. They are controlled centrally via the Intune Admin Centre.
Windows Autopatch creates its own policies for Windows feature updates, cumulative updates, driver and firmware updates. It is configured via the Microsoft Graph API; for end devices, it is configured via Windows Update for Business. This means that the service fits seamlessly into the existing MDM architecture with Intune.
Licensing
No separate licence is required to use Windows Autopatch. The service is included in the following Microsoft plans:
- Microsoft 365 Business Premium (incl. Windows 10/11 Business)
- Microsoft 365 F3 (incl. Windows 10/11 Enterprise E3)
- Microsoft 365 A3, A5 (incl. Windows 10/11 Education A3, A5)
- Microsoft 365 E3, E5 (incl. Windows 10/11 Enterprise E3, E5 (also VDA))
Comparison with classic update solutions
Windows Autopatch aims to relieve IT teams of everyday tasks. The service takes over recurring tasks, ensures consistent update statuses and reduces the effort required for planning, monitoring and troubleshooting. This leaves more time for strategic issues in device management.
In comparison to classic solutions such as WSUS or Windows Update for Business, Windows Autopatch offers a significantly higher level of automation and integration. The differences at a glance:
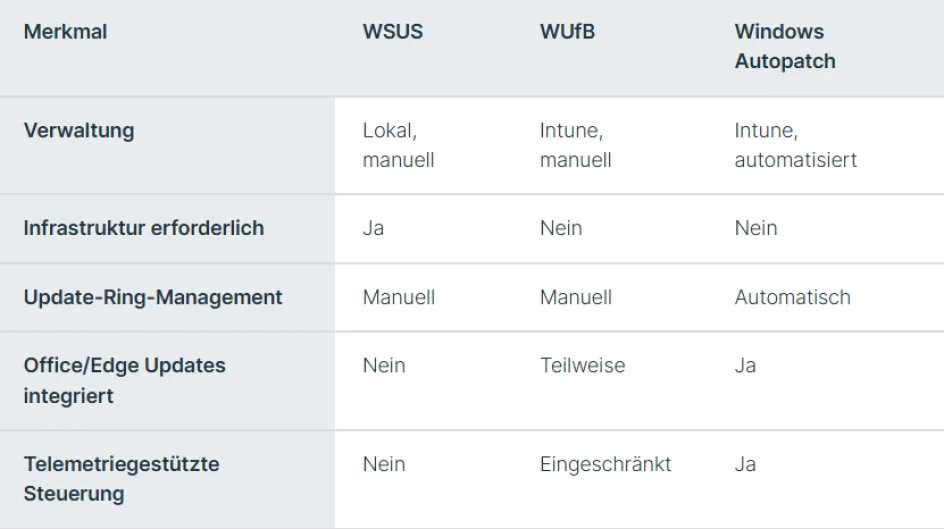
Features and benefits of Windows Autopatch
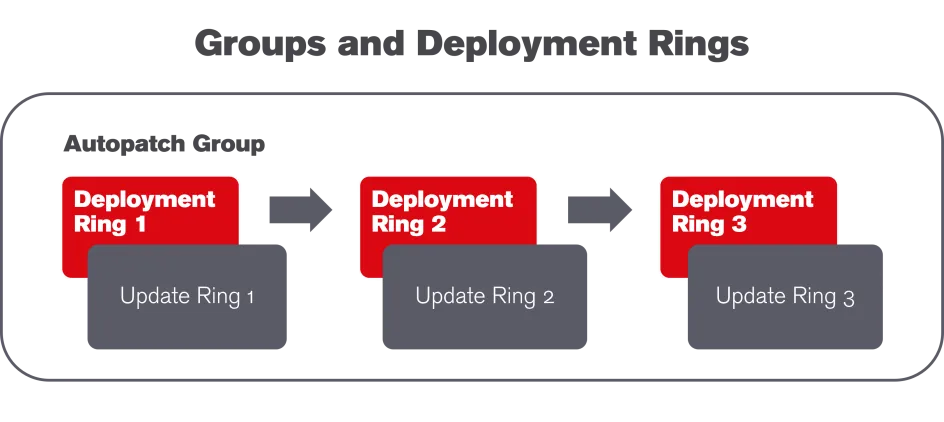
Autopatch Groups & Deployment Rings
Windows Autopatch automates the distribution of updates via so-called Autopatch Groups. Devices, policies and therefore configurations for Windows, Microsoft 365 Apps and Microsoft Edge are bundled in these groups. Within each Autopatch Group, devices are divided into so-called Deployment Rings, i.e. into stages that receive updates one after the other. These rings can be filled statically (with fixed device groups) or dynamically (distributed on a percentage basis). Devices can be manually moved to another ring at any time, for example for specific tests or because it is the managing director's device. Behind each deployment ring is an update ring, which defines the specific configuration, such as the installation time, deadlines and restart behaviour. All settings are based on familiar Intune functionalities. However, Windows Autopatch considerably simplifies the management of multiple update rings.
The behaviour on the end device is determined by the Update Deployment Cadence . This determines when an update is offered to a device and whether updates are installed at a fixed time or only on a deadline basis (Update Deadline). In addition, the Grace Period regulates how much time remains after the deadline until the forced restart. Thanks to Delivery Optimisation, Windows distributes updates efficiently in the local network, often via peer-to-peer connections. This speeds up distribution and reduces internet bandwidth requirements.
Supported update types
Windows Autopatch supports a wide range of update types, including:
- Windows Feature Updates (incl. predefined rollout phases)
- Windows Quality Updates (cumulative updates)
- Hotpatch Updates (without reboot)
- Accelerated Quality Updates
- Recommended firmware and driver updates
- Other firmware and driver updates
- Microsoft 365 Apps Updates (Office Updates)
- Microsoft Edge Updates
Autopatch Service Level Objective & Monitoring
A central element of Windows Autopatch is the Service Level Objective (SLO). It specifies that at least 95% of active devices must be supplied with the latest quality update within a defined period of time. This creates a clearly measurable target that ensures both transparency and quality assurance in update management.
The integrated telemetry and monitoring continuously provide data on the status of the devices, the progress of the updates and policy compliance. The devices are assigned one of three statuses: Up to date, In progress or Not up to date. This information can be traced back over a period of 90 days. In the event of problems, the system automatically displays the causes and recommended measures. The Autopatch Policy Health and Remediation function recognises incorrect configurations in the Autopatch service and corrects them automatically.
These mechanisms significantly reduce Windows Autopatch downtimes and security risks. Critical security updates reach devices faster and, thanks to hotpatch, without the need for IT teams to intervene manually. At the same time, the risk of incompatibilities is reduced as new updates are first tested in small rings. IT stays informed, retains control and can focus on other tasks at the same time.
New functions and developments in Windows Autopatch (2025)
Windows Autopatch is constantly evolving and now combines all cloud-based update functions under one name. The previously required feature activation is no longer necessary - Autopatch is now fully integrated into Intune and ready for immediate use. The familiar Autopatch Groups and Deployment Rings remain and offer additional functions.
Predefined Deployment Ring Presets
Deployment Rings can now be set up via predefined presets, which simplifies typical update scenarios and makes the update deployment cadence customisable without manual settings. Available presets:
- Information worker: Devices of users who primarily work with digital information
- Shared devices: shared devices
- Kiosks and billboards: Kiosk devices or digital billboards
- Reboot-sensitive devices: Devices that are sensitive to reboots
Expanded update coverage
Microsoft 365 Apps Updates (Office Updates) and Microsoft Edge Updates are now fully integrated into Autopatch. They follow similar rules to Windows Updates and can be controlled uniformly via the familiar deployment rings.
RBAC & improved reporting
The new RBAC model (Role-Based Access Control) enables a more detailed assignment of rights. For example, the "Windows Autopatch Administrator" role can manage all aspects, while the "Windows Autopatch Reader" role only allows read access. In this way, tasks can be clearly separated, for example between central IT and decentralised admins.
The reports have been expanded and now not only show the status, but also:
- Trends and policy deviations
- Devices with repeated errors
- Progress per deployment ring
In addition, the reporting duration has been reduced from over a day to just four hours. This means that problems can be identified and dealt with more quickly and the update strategy can be optimised based on data.
Conclusion: Why the time is now ripe for Windows Autopatch
Windows Autopatch noticeably simplifies update management. It automates the distribution of Windows patches, recognises problems at an early stage and fixes them - for example, by automatically correcting policies or retriggering failed updates. The solution utilises familiar functions from Endpoint Management with Microsoft Intune, but extends these with intelligent mechanisms: devices receive updates in stages via granularly controllable rings, reports show the status promptly and policies can be controlled simultaneously from a single location. Security and operations also benefit from clearly defined responsibilities and a higher degree of automation.
This makes Windows Autopatch an innovative, future-proof solution that offers considerable advantages, especially for companies with around 100 employees or more. Anyone embarking on the journey should check which devices and groups are suitable for getting started and what the requirements are in terms of processes and governance.
Those planning an introduction can use the following questions as a guide:
- What does Windows Autopatch need to be able to do so that we as an organisation are prepared to relinquish some control - and become better in the process?
- Which devices are suitable for getting started?
- Which groups of devices need special rules?
These are precisely the points where we at Claranet come in and support companies in successfully introducing and sustainably operating Windows Autopatch.
Claranet as a partner for modern Windows update management
As an experienced Microsoft partner in the field of endpoint management, we support you in the introduction of Windows Autopatch - from analysis and design to implementation and operation. Our goal: update processes that integrate seamlessly into everyday working life.
A practical example shows what this can look like: An international company with tens of thousands of Windows devices was faced with the challenge of distributing updates more efficiently and consistently worldwide. After a successful feasibility study, we initially worked together to establish Intune and Windows Update for Business for Windows Feature Updates. In a subsequent test run, we demonstrated how Windows Autopatch simplifies the management of security, firmware and driver updates. On this basis, we developed a globally applicable update strategy that significantly reduces the dependency on manual processes and enables a global, staggered rollout across defined device groups. As a result, the customer will benefit from approximately 50-65% shorter update cycles, clearer reports and noticeably less effort in day-to-day IT work.
We offer consulting, implementation and managed services from a single source. Request your free consultation now - directly via our contact form. Together we will clarify whether Windows Autopatch fits your environment and which steps make sense during the implementation.
Event: Microsoft 365 & Endpoint Management under control
Tip: Would you like to delve even deeper into the topic of endpoint management?
Visit our event "Modern, secure, resilient: Microsoft 365 Endpoint Management under control" and find out how you can optimise your endpoint environment holistically.
