Security Operations Centre (SOC): Basics, costs and benefits
What is a Security Operations Centre
A Security Operations Centre (SOC) is a central unit responsible for monitoring, analysing and defending against cyber threats within an organisation. Cyber attacks are increasing in frequency and sophistication. As an essential part of a robust cyber security strategy, a SOC helps to detect attackers early before they can cause significant damage.
In this blog post, we look at who needs a SOC and how it works. We also compare the benefits and challenges of setting up an in-house SOC with outsourcing to a managed service provider and look at the financial factors of both options.
Who needs a SOC?
Cyber attacks have become the number one threat to organisations, regardless of their size or industry. The damage caused is diverse and affects many unexpectedly:
- Operational downtime: Paralysed IT systems lead to a loss of productivity. Restoring the systems can take time and resources.
- Financial losses: In addition to losses due to operational downtime, further financial losses can result from the theft of funds or extortion through ransomware.
- Data loss: Business secrets, intellectual property or customer data can be leaked or permanently lost.
- Legal consequences: Data breaches can result in penalties and claims for damages.
- Reputational damage: A successful cyber attack can negatively impact the trust and reputation of the affected company with customers, partners and the public.
Many companies take preventive security measures to avoid such scenarios. However, practice shows that a successful attack is often only a matter of time. Once affected, many questions arise: How did the attackers get into the system? Which systems are affected? What data has been lost? Has personal data been leaked? Is a report to the data protection authority necessary? And what information must be provided there? If these questions cannot be answered, there may even be legal consequences under the GDPR, KRITIS laws of the BSI or NIS-2.
A Security Operations Center makes a significant contribution to detecting potential attacks at an early stage, responding to them and minimising potential damage. In the best-case scenario, the questions above do not even arise thanks to a SOC. In addition, the process and scope of the affected systems and data can be precisely specified in the event of an attack.
The short answer is therefore: every company that wants to protect its IT infrastructure and business-critical data and be prepared for an emergency should consider implementing a SOC.
How does a SOC work?
Cyber attacks usually take place in several phases: from reconnaissance of the target and identification of suitable attack methods to initial attacks and the installation of a bridgehead through to control of the target systems (see, for example, Lockheed Martin's Cyber Kill Chain®). A look at the statistics shows that attackers can often move around the system for weeks to months after the initial intrusion before they are discovered. In doing so, the attackers create traces that are reflected as digital footprints in the logs of the affected systems.
A Security Operations Centre is designed to detect and stop attackers at every stage based on their traces before they can cause any damage. The SOC essentially consists of a team of IT security experts who monitor a company's IT infrastructure around the clock.
Technologies and processes in a SOC
As a rule, a SIEM (Security Information and Event Management) plays a central role in the Security Operations Centre. The SIEM analyses the log data of all relevant systems in the network. These can be servers, firewalls, network devices, end devices or applications. If a suspicious pattern or behaviour is detected, an alarm is triggered. This is analysed and prioritised by a SOC analyst within a few minutes. They decide whether it is a false alarm or an actual threat and initiate further steps.
In addition, EDR solutions (Endpoint Detection and Response) can be used. These run directly on the endpoints, such as desktops or laptops, and continuously analyse the activities taking place there. If a suspicious process is detected, it can be terminated automatically. For example, ransomware can be detected and stopped before any damage is done.
One of the main challenges in operating a SOC is to continuously improve the detection rate while reducing false alerts. Too many false alerts lead to SOC analyst fatigue, while actual attacks can be overlooked if visibility is too low. The systems used must therefore be continuously maintained and optimised in order to ensure efficient and effective operation.
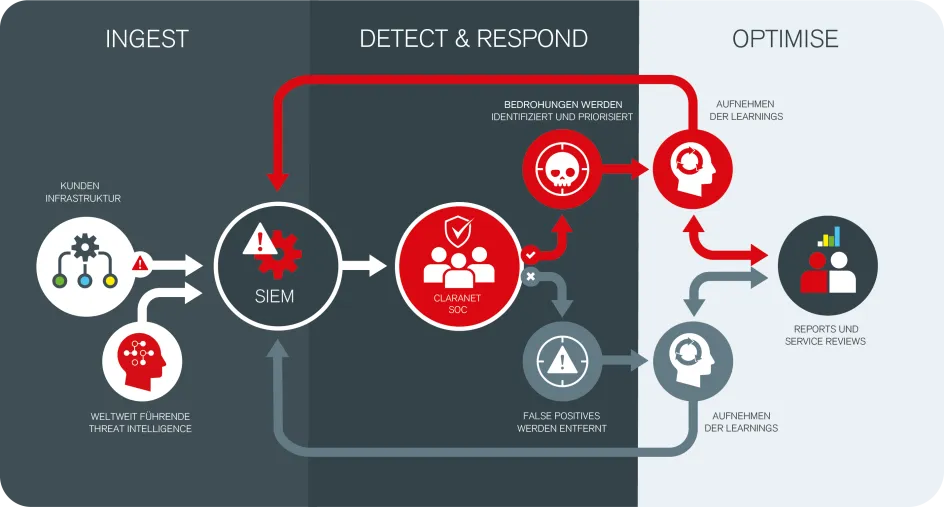
Features and functionality of a SOC using the example of the Claranet Managed SOC
Roles in a SOC
In addition to the processes, a SOC consists of clearly defined roles for the team members:
- SOC analysts continuously analyse and prioritise incoming alarms and initiate countermeasures.
- SOC Engineers take care of the development, implementation and maintenance of the SOC's technical infrastructure.
- SOC Managers manage the budget and personnel. They are also the interface to other responsible parties in the company.
There are often other roles, such as shift leads or threat hunters, who proactively search for threats. The specific distribution of roles can vary depending on the SOC. In any case, the processes and roles of the team members are clearly defined to ensure that the company is effectively protected against cyber attacks around the clock.
How does a SOC work in practice?
In this one-hour deep dive video, Tom Kinnaird (Cyber Services Practice Lead at Claranet UK) uses a simulated attack to show how a SOC can recognise and fend off an attack in practice:
In-House vs. Managed SOC
When setting up a security operations centre, companies are faced with the decision between an in-house and a managed SOC service.
An in-house SOC is set up and operated by the company itself. It offers complete control and can be customised to suit individual requirements. A major challenge when setting up an in-house SOC is the recruitment of qualified personnel. According to the SANS 2023 SOC Survey, a SOC size of 11 to 25 team members is the most common, with larger companies having up to 100.
A managed SOC is operated by an external service provider. Cyber security experts ensure monitoring and maximum response speed around the clock (Managed Detection and Response, MDR). However, companies must relinquish some control over their IT systems and find a suitable provider that meets their requirements. Once booked, a managed SOC offers maximum flexibility and scalability.
The choice between an in-house SOC and a managed SOC ultimately depends on a company's specific requirements and resources. In any case, we recommend that you carefully determine and compare the total costs for both options.
Total cost consideration and return on investment
The decision to opt for a security operations centre is associated with significant investments that many companies initially shy away from.
For a differentiated consideration, it is important to first look at the total costs (Total Cost of Ownership, TCO). While the costs of a managed SOC can be read from the respective provider's offer, determining the total costs of an in-house SOC requires totalling all costs for setup and operation. This includes costs for personnel, technology, software licences and premises, as well as ongoing costs for the further development of systems and employees. In most cases, the final sum is higher than the costs of specialised managed SOC providers, who benefit from economies of scale, among other things. Another advantage of booking a managed SOC is that expenditure is easier to plan.
When investing in IT security, however, a purely cost-based approach falls short. IT security is not an end in itself, but rather an essential investment in a successful future. A SOC helps you to reduce potential damage caused by cyber attacks and the associated costs due to losses, downtime, reputational damage or legal consequences. In business administration, the return on investment (ROI) is often calculated when considering the quantifiable benefits of an investment. This involves comparing the return on an investment with the associated costs. As security investments do not generate any direct returns, the classic definition falls short. An interesting alternative is the Return on Security Investment (RoSI). The key figure aims to determine how much damage could be avoided by the IT security investment.
Conclusion
A security operations centre is an indispensable component of an effective cyber security strategy. By looking at the overall costs and benefits, it becomes clear that the decision in favour of a SOC is a sensible and profitable investment. Both in-house and managed SOCs offer advantages. Companies should choose the operating model that best suits their requirements.
Practical check: Which SOC solutions are best for my company?
The rapid development of new technologies and the multitude of solution approaches do not always make it easy for decision-makers to find the right strategy. Many people ask themselves:
- Which technical solutions are best suited to my company?
- How can they be implemented and integrated into existing structures?
- What impact does a SOC have on my employees and processes?
- Do I build it myself or do I rely on a specialised provider?
- And last but not least: What will the whole thing cost?
The "Claranet SOC Assessment Workshop" helps you to find your way through the jungle of options: Together, we analyse your requirements and risks in order to develop the optimal combination of technologies, processes and competencies.
