Who bears responsibility in the public cloud?

Ingo Rill
Strategic Communications
The accelerated pace of innovation, increased customer expectations in terms of performance and global availability of services are key challenges for companies today. This is where public cloud platforms can help: They offer virtually unlimited resources, a wealth of platform services and the desired international footprint. However, in order to utilise the potential of hyperscalers such as AWS, Google Cloud or Azure, a number of requirements need to be taken into account. This applies in particular to the security of the systems used. The key question is who is responsible for which areas in the public cloud.
Responsibilities in the public cloud: desire and reality
Whether out of ignorance, orientation towards classic outsourcing models or the desire to be comprehensively relieved: Many companies see the public cloud provider as being responsible for tasks that are not within its remit. A study by Crisp Research on the "Distribution of responsibility in the public cloud" shows that for most companies, the public cloud provider is responsible in almost all areas.
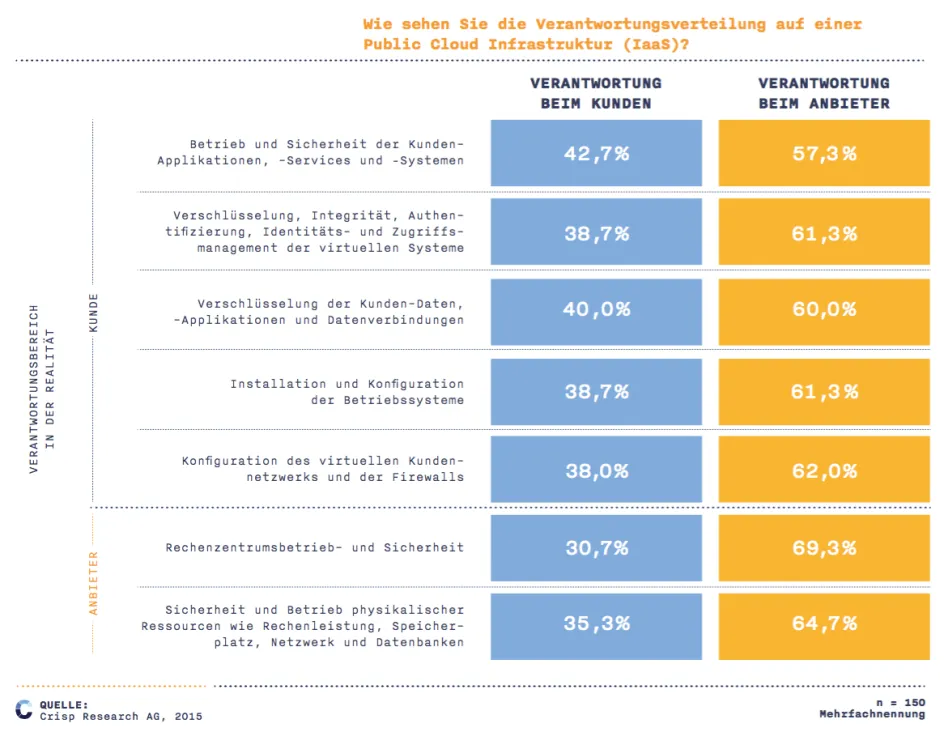
Although this is certainly the more convenient option for the customer, it is still a misjudgement: the public cloud provider is not responsible for the security and management of all service layers.
The "shared responsibility" model
In terms of the security and management of public cloud services, the "shared responsibility" model applies. The public cloud provider is not responsible for the entire service stack up to the application level, but only for the infrastructure, i.e. the hardware, network and facilities on which cloud services are executed. The customer's area of responsibility extends to the operation and security of their own infrastructure environment and the systems, applications, services and data operated on it.
Examples of the responsibility of the public cloud provider
- Structure of the physical locations and data centre infrastructure
- Computing power, storage space, network
- Provision of the virtualisation layer
- Provision of services and tools
Examples of customer responsibility
- Installation and security of operating systems including updates and patches
- Security and management of application software
- Configuration of the firewall
- Encryption of data and data connections
- Identity and access controls
- Security and access controls
- Security and security of application software
- Configuration of the firewall
- Encryption of data and data connections
- Identity and access controls
- Security and and access controls
- Operating your own applications
AWS differentiates in this sense, for example, between "security of the cloud" and "security in the cloud". "Security of the cloud" refers to the protection of the infrastructure in which the services offered in the AWS Cloud are executed. "Security in the cloud", on the other hand, addresses the responsibility of the customer, for example the application software or utilities they use. It is also relevant which specific services of a public cloud provider the customer uses, as the responsibilities may vary depending on this.
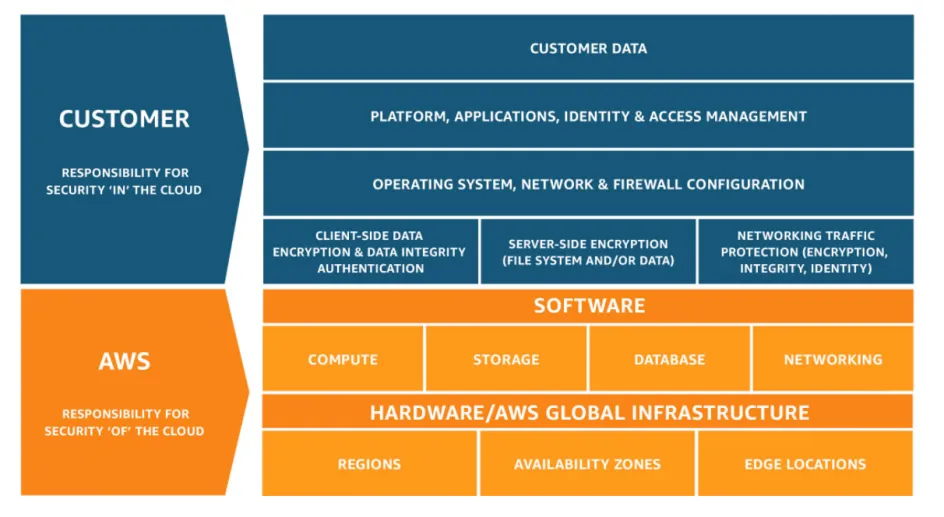
AWS has formulated the shared responsibility model most explicitly, but the other hyperscalers also follow a similar approach - Google Cloud Platform and Microsoft Azure also assume a model of shared responsibility between provider and customer.
Avoid risks - seize opportunities
An incident from July 2017 illustrates what can happen if you ignore your own responsibility for security in the public cloud. The data of several million customers was accessible for months on an unsecured cloud server at a Verizon service provider. The reason was inadequate security measures on the customer side.
This example and similar incidents prove that it is necessary to be aware of your responsibilities and to sufficiently understand the service portfolio and the characteristics of the cloud platforms. Public cloud services are neither a simple new edition of classic outsourcing, where responsibility for security is also delegated, nor are they "IT resources from the socket". Secure and efficient use is only guaranteed if companies implement the necessary measures themselves or have them implemented by a specialised partner. Only then can the opportunities and benefits of the public cloud be successfully exploited for the digitalisation of the company or to gain cost advantages.
