WTF does a SOC actually do?

Tom Kinnaird
Head of Security Product Engineering
If someone robbed your house, you would probably find out when you got home. Signs of forced entry, furniture overturned, drawers opened and belongings strewn everywhere, while the thieves sought whatever valuable goods you owned. It would take an exceptionally skilled and motivated thief to break into your house, get past the burglar alarms, find the keys to your safe, take your valuables and leave without a trace.
However, this is often what happens with cyber attacks. Some organisations only find out about a security incident when the police contact them explaining they have encountered that company's sensitive data for sale on the dark web.
Basic protections like firewalls, password policies, multi-factor authentication and phishing training will protect against most low-level attacks. For more advanced threat actors however, getting past these defences and other network security controls is only the first step. They must snoop around, looking for what they can steal, encrypt, hold to ransom or deface, without raising suspicion from the SIEM or Endpoint Detection and Response tooling.
Even these highly sophisticated attack detection tools require human operators to discern real cyber attacks from false alarms and determine the best response. And the need for a discerning and experienced human increases as attackers’ dwell time – how long they spend on your network before finalising their attack – goes down.
Our knight in shining armour is known as a Security Operations Centre (SOC). In this blog, we will break down exactly what a SOC does, how they detect cyber attacks, why you need one, and how they bring value to your organisation.
Catch me if you can
Most organisations still struggle to detect cyber attacks until the worst has already happened. Why?
Complex and ever changing IT systems | Detecting cyber attacks is difficult. The growing complexity and ever-changing nature of our IT systems works to the attacker’s advantage. An ever-changing attack surface is difficult to monitor and defend, making it easier for attackers to establish a foothold and launch their attack undetected. |
The volume of false positives | Without being properly configured to your organisation’s IT estate and its data, SIEM tooling can generate a deluge of false positive alerts. Without a dedicated team who can triage all events, filter out the false positives and then fine-tune the SIEM to generate fewer of them, organisations can find their fancy SIEM tooling becoming a burden. |
Attack techniques evolve every time you update your defences | New attack techniques emerge weekly and legacy anti-virus systems (which use signal-based detection methods) can only detect indicators of compromise after the vendor has updated them i.e., after those attack techniques become widely-known because attackers are already using them and other companies are already falling victim to cyberattacks. |
The cybersecurity skills gap makes it hard to find the right talent | Many companies lack the security expertise necessary to research, analyse, and understand emerging threats, leaving them under-prepared to effectively respond to cyber-attacks. |
Building and maintaining an in-house SOC is too costly for most organisations | Trying to build and maintain an in-house security team with the necessary security skills is too expensive for the IT budget of most organisations. |
For organisations, these challenges add up to the age-old dilemma: build it or buy it? To answer that question, they need to know first exactly what a SOC does.
A detective on the trail
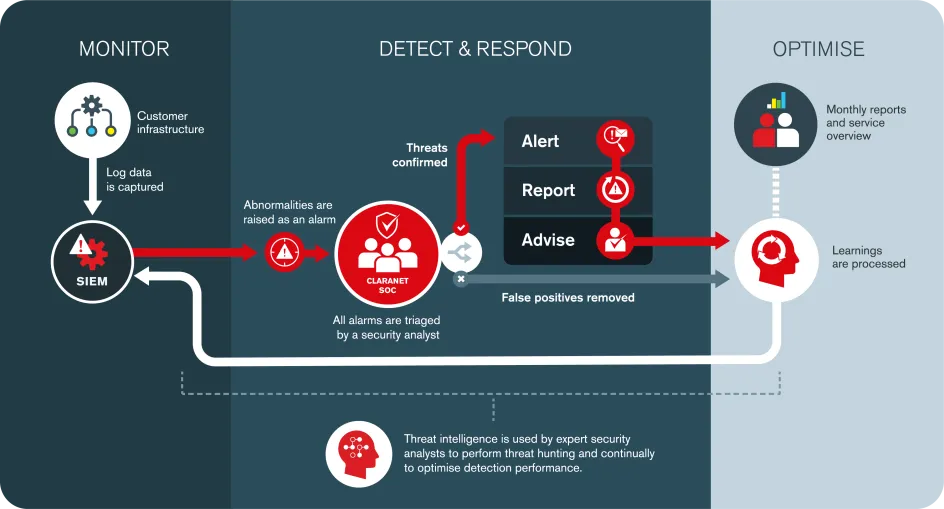
Fig. 1, Example of how a SIEM platform collects data and the triage process for SOC analysts
Your EDR or MDR tool collects logs on user behaviour, then analyses them to determine whether the behaviour looks suspicious. But suspicious-looking behaviour can often be a false positive generated by the day-to-day activities of your users. Maybe a new device has just been onboarded to your network, or someone has logged on during a business trip, and their IP address is in another country. SOC analysts monitor these alerts 24/7/365. The first step is to determine whether the alert is a false positive or a genuine Indicator of Compromise (IoC), suggesting the work of cybercriminals.
The second step is to determine what happened and why the alert was generated. This is where the real detective work comes in. Is it one infected device or multiple infected devices? Has any customer data been compromised? Your SOC should present you with the relevant evidence about the nature of the compromise and advise you how to defend yourself if the attack is still in progress, or they can take defensive actions on your behalf, such as containing an endpoint or disabling a user’s account. But piecing together the puzzle and tracking down the culprit requires experience and threat intelligence.
Threat intelligence can take different forms (strategic, tactical, technical and operational) and can come from multiple sources. Threat intelligence feeds contain Indicators of Compromise (such as IP addresses, domains, file hashes) that might have been used in cyber attacks previously.
- Open-source threat intelligence is shared by cyber defenders, MSSPs and tech giants like Microsoft for the good of all mankind. You can search for an IP address and see whether the information in this alert has been used elsewhere in other attacks.
- Closed threat intelligence feeds normally come from the data captured by the SOC in your chosen MSSP. They include information about cyber attacks from other customers. The tactics, techniques and procedures used in these attacks can be fed into the SIEM to enrich alerts you get next time.
Against the clock
Speed matters when it comes to detecting cyber attacks. To limit the damage and avoid the worst consequences, you need to act fast. Having access to threat intelligence speeds up the investigation. But theory and book-smarts can only go so far. It must be augmented by practical experience. SOC analysts don’t just work out what happened and how the attacker got there – they are battle strategists.
Depending on what services you employ (whether it’s EDR, MDR or XDR) your SOC can either advise you what to do next, or they can take action on your behalf to quarantine the attacker and remove them from the network. The ability to make the right judgment call, and quickly, can only come from experience of seeing a wide range of cyber attacks across a variety of companies and industries. In some cases, depending on how far the attack has progressed, your SOC may advise you to involve a specialist Incident Response provider.
SOC analysts use a variety of tools to build a complete picture of the attack which has taken place, but without a SIEM, it can be difficult to know exactly what has been accessed, compromised, or stolen. But without a skilled SOC analyst monitoring your SIEM and fine-tuning it over time, it can be difficult to catch cyber attacks still in progress, before they inflict the worst damage.
After the storm has passed
Quarantining the threat is the last step in stopping a threat actor. Then it’s about filling in the blanks, finding all the missing pieces. A file containing malware doesn’t just magically appear. A random user gaining and using Domain Admin privileges should be picked up by your SIEM. In the review after a cyber attack, SOC analysts try to understand exactly how the attacker gained a foothold and progressed their attack from one stage to the next.
They might ask questions like: Did our detection rules pick it up? Did we detect the entire attack chain? One attack could be made up of ten, twelve, fifteen different parts. Where did we find it on that attack chain? If we found it in the middle, why didn’t we pick it up at the start? What attack techniques and tools was the threat actor using that evaded our detection rules?
SOC teams use this information to provide you with remediation advice. Heed it. Patch the vulnerabilities the threat actor exploited and/or make the necessary changes to your IT estate, so that you are unlikely to be compromised by the same attacks again. Likewise, they will fine-tune the detection rules on your SIEM platform to ensure that any attack techniques or Indicators of Compromise that the SIEM missed, will be caught next time around.
The exciting part is seeing something new: a zero-day exploit or some new attack technique rarely seen in the wild. From this investigation, SOC analysts may be able to piece together roughly who conducted the cyber attack, if the Indicators of Compromise, and the attack techniques used resemble those of a known cybercriminal group or Advanced Persistent Threat (APT). Whenever new attack techniques are discovered, cyber defenders and MSSPs sometimes share this as open-source threat intelligence, though the information is often anonymised as part of their contract with the client.
On the hunt
But what if attackers do slip through the net? We mentioned exceptionally skilled attackers and Advanced Persistent Threats. Some can evade attack detection tools like Endpoint Detection and Response and Managed Detection and Response to lie in wait, conducting internal reconnaissance. For these we have threat hunting.
By understanding how attackers think and act, threat hunters form hypotheses about new attacker techniques, and look for attackers that have slipped past your attack detection tools and other network security controls. Threat hunters make sure you are looking for the unseen, so that you aren’t just responding to incidents to defend yourself after the cyber attack has begun.
How did I do?
The final part of the post-incident review is an evaluation of the response. How good was our response to the attack? When reviewing an incident, it’s imperative to sing the praises of things going right, as well as taking a good hard look at what can be improved in future.
As well as reviewing the play-by-play of a cyber attack, your SOC should conduct regular reviews, usually monthly and quarterly. During these reviews they can help you:
- Reduce false positives. SOC analysts should work with you to understand why false positive alerts were generated so they can fine-tune your SIEM. But this may involve some work on your side too: SOC analysts will advise what actions you can take to make sure that those false positive alerts don’t come through again. This might mean tightening up IT security policies and procedures internally. Lowering the number of false positives reduces the potential for alert fatigue and means that real alerts can be spotted faster.
- Ensure you’re getting the coverage you need
- Understand how future changes to your IT estate will affect your attack surface and what attackers are likely to target.
At this stage, client relationships make all the difference. Understanding what your IT estate looks like, and understanding what systems are in place helps SOC teams make faster, more accurate decisions in the heat of battle.
From reactive to proactive defence
As well as providing defensive actions in the midst of a cyber incident, SOC teams also perform a range of proactive services such as:
- Running threat modelling exercises to determine what attack techniques you are likely to face and why
- Developing and fine-tuning the detection rules on your SIEM
- Improving coverage across your network
- Implementing automations on your SIEM and EDR tooling to speed up the triage process
- Threat hunting to scour your network for attackers that may slip through the net
Your SOC is there to defend you before, during and after cyber incidents. Working hand in hand with your SOC and consulting them about your defensive strategy will pay dividends for your cybersecurity.
To find out more about how you can improve your security posture and your ability to respond to a cyber-attack, get in touch about our Endpoint Detection and Response and our Managed Detection and Response services.
