What is penetration testing?
The digital age has come and gone. Right here today, we’re living in the post-digital era. Applications and systems are no longer fast becoming a core part of business, they are now the foundation of the world’s business ecosystem. And rather than software “users”, most organisations are now technology companies in their own right; application design, development, and implementation form the backbone of operability and growth. It’s an exciting time to be doing business.
Naturally though, within dynamic, multiplex digital infrastructures where business is driven by development lifecycles, applications accumulate and cyber risk evolves fast. Development and scale provide the opportunity for organisations, but also for a greater number of attackers set to monopolise on this accumulation. The emergence of new risk is continuous, magnified by the increased accessibility of attacker tradecraft. This leads us to an important question: how do you scale your security testing activities to rival the growing risk?
Penetration testing has always been a core building block of cybersecurity, and with more applications and systems to test than ever before, that remains the case. But the industry is moving forward and the playing field for testing is changing. In response, this article takes a deep dive into penetration testing – what it is, how it’s best used, and where it fits alongside new, continuous approaches to testing.
What is penetration testing?
Penetration testing (aka pentesting; pen testing) is an offensive security exercise that uses manual and automated (tooling-based) techniques to design and deploy a controlled attack on an organisation's assets to test their security. “Security” in this context is defined by the resilience of said assets – i.e., their ability to withstand different malicious techniques being used against them to:
- Harm them (corrupt, destroy, or encrypt)
- Extract information and secrets
- Manipulate them into means for targeting further assets
The deliverable of a penetration test is a report. This provides details on the security of the tested assets so that the organisation undergoing testing can remediate vulnerabilities and bugs and improve their application implementation and governance processes.
Penetration testing is a point-in-time activity: it evaluates the security of an asset at an exact moment. Unlike the continuous security testing activities discussed later in this article, it is not designed to be dynamic.
Why do I need to do penetration testing?
Penetration testing is just one of many activities required within a robust, resilience-focused security strategy. At a high level, organisations need penetration testing because it highlights asset-based weaknesses present on an attack surface. Viewed in a practical business context, this can lead to many positive outcomes:
Risk management
Outcome: monitor, control, and minimise the likelihood, severity, and impact of a cyberattack against the organisation; maintain business continuity during an attack.
Compliance
Outcome: establish and/or maintain regulatory compliance to avoid penalties; develop customer trust and gain a competitive advantage as a compliance-led organisation.
Digital transformation
Outcome: achieve maximum return on investment (ROI) from digital transformation projects by verifying the safety and security of new technologies and the processes underpinning their implementation.
Brand protection
Outcome: avoid or reduce reputational damage and the associated financial implications following a compromise.
Partner/customer demand
Outcome: achieve business growth by fulfilling partner security testing requirements.
Who carries out penetration tests?
Penetration tests are carried out by penetration testers (aka pentesters; pen testers; security testers). Pentesters normally work for security vendors and managed security services providers (MSSPs), but sometimes exist client-side in an internal team. They are offensive (rather than defensive) security specialists trained to tackle security from an attacker’s perspective.
A penetration tester’s job isn’t simply to test in isolation. Much of their work is communication and consultation. They will discuss the logic behind their thinking, advise based on previous experience, and call on specialists in their team when additional expertise is needed.
It’s important to understand the level of service your provider can offer through its pentesters, as this will inform the accuracy of the test, the thoroughness of the report you receive, and your experience throughout. Accreditation is one way to validate the calibre of a pentesting team. Further evidence can be gathered from examples of:
- Complex and bespoke engagements tailored to a client’s needs (case studies)
- Offensive research and tooling development
- Independent research, authoring, and public knowledge sharing
How are penetration tests carried out?
Penetration testing varies from company to company, but the typical flow of activities covers the following six steps:
Pre-test
1. Scoping and planning
A project scope and plan are used to model the test around the organisation’s requirements as per the outcomes it is trying to achieve. These are agreed between customer-side stakeholders and an experienced member (or members) of the penetration testing team, leading to a scope of work that will include:
- Penetration test goals and desired business outcomes
- Systems, applications, or infrastructure in scope (to be tested)
- Testing methodology
- Testing location (onsite/remotely)
- Project duration
- Confirmation of critical assets and sensitive files
- Confirmation of any exclusions
Once the scope of work is agreed upon, the provider will recommend a statement of work. This sets all expectations for the test, including the cost.
2. Preparation
A penetration tester will be allocated to the project and the work time scheduled by the provider’s delivery management team. Timescales, system access, channels/frequency of communication, and agreed safety measures will be submitted to the customer for approval. This approval provides the “authority to test” – the official consent from the customer and any required third parties for the provider to begin testing as agreed in the statement of work.
Test
3. Reconnaissance
As an offensive security assessment, penetration testing broadly follows the cyber kill chain. As such, the tester will start by performing reconnaissance to analyse the asset(s) in scope. Reconnaissance involves network scanning and application mapping to build context and identify potential vulnerabilities within the asset(s). This stage is essential for the tester to accurately understand how the asset(s) are connected to the organisation’s wider infrastructure and what potential risk they pose in that context.
4. Manual testing
Following reconnaissance, the pentester will select the most suitable techniques and design an attack sequence to achieve the objectives outlined in the statement of work. This can involve any number of techniques to exploit individual vulnerabilities within the asset(s) and chain vulnerabilities together to demonstrate how one technique can be scaled. Unlike red teaming, where activity is delivered covertly, pentesters typically work overtly without a limit on the attempts they can make to compromise the asset(s).
The approaches used by a pentester during this stage will be tied to attack methodology, whether or not their tactics, techniques, and procedures (TTPs) have been seen executed in the wild. This type of experimentation enables organisations to see how unfamiliar and novel techniques could be used against them in a real attack scenario, increasing the realism of the test.
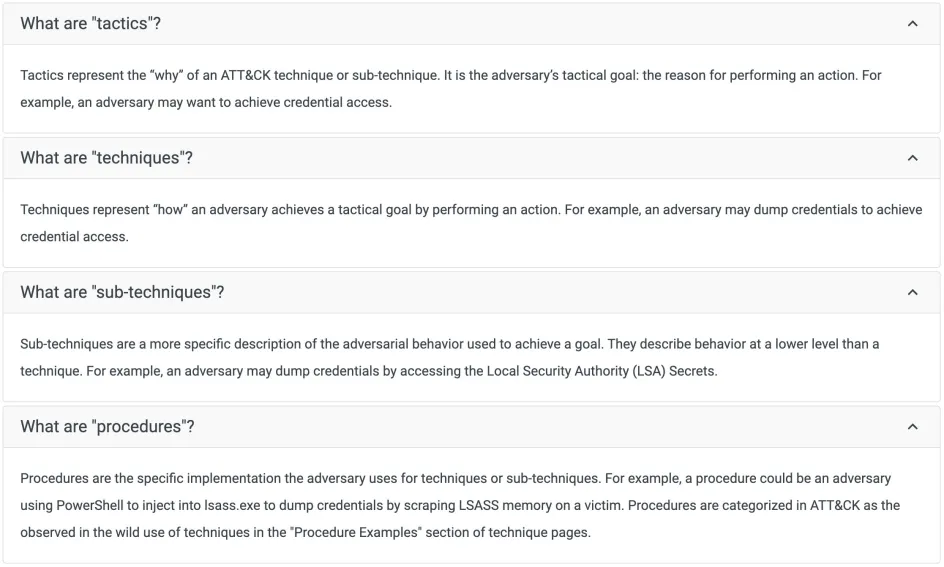
Ref: MITRE definition of “TTPs”
Review
5. Analysing the test
Once the test is complete, the pentester will measure its success and document their findings by processing the raw data to give it context for the customer. Their thinking will cover:
- The techniques they used and how
- A justification of the reasoning behind the approach
- How their findings translate to business risk, as well as the other business outcomes concerning the customer
- Further findings about the customer’s overarching security architecture
The objectives outlined in the scope of work should form the basis of any analysis and the report that follows.
6. Reporting
A pentesting report will typically contain the following information:
- A list of the security vulnerabilities identified, including a score (usually based on the Common Vulnerability Scoring System (CVSS))
- An assessment of the level of risk created by each vulnerability
- Suggestions for remediating vulnerabilities (through reconfiguration, patching, etc.)
- An holistic analysis of the business’s overall IT security
- Broader vulnerability management advice
The remediation work following a test normally falls out of scope. If re-testing was included, however, there will be discussions around how and when this should take place.
Is penetration testing safe?
Any live assessment carries the risk of disruption to systems, but these can be managed and reduced. During scoping discussions, agreements should be made around the precautions necessary to maintain stability and safety, such as:
- DoS/DDoS activities being excluded from the scope of work.
- Unstable exploits being executed only after proper approval has been supplied.
- Testing on development or staging platforms.
Penetration testing types
Penetration testing is a huge area within cybersecurity, so there are many variables and approaches. The starting point for any testing project is, however, the objective, followed by the asset type or environment.
| Asset/environment | Typical assessment areas |
| Web Application and API testing |
|
| Mobile application testing |
|
| Infrastructure (network) testing |
|
| Cloud infrastructure testing |
|
Penetration testing is also sometimes described in the context of black box, grey box, and white box methodologies. These can be explained as follows:
| Type | Execution | Benefits/use |
| White box (open box) | The tester is given full access to information on the target asset/environment. | Enables a test to utilise as many attack vectors as possible. Example use case: attempting to understand the associated risks with implementing a new tool. |
| Grey box (collaborative) | The tester is given limited information, such as a user’s login credentials. | Balances realism with efficiency by cutting out some parts of the process. Example use case: simulating how an attacker would traverse the network having successfully stolen a user’s credentials. |
| Black box (closed box) | The pentester has no prior knowledge of the target asset(s). The test is led by the findings of their initial reconnaissance. | Most realistically mimics an attack. Example use case: calculating the organisation’s overall risk profile according to the susceptibility of its critical assets to exploitation. |
To ensure the right type of test is selected, an organisation’s security team must start with a risk-centric mindset tied to a business problem/goal. During the scoping and planning stage, this will help the pentesting provider devise a suitable hypothesis and build a test around that.
What are the outcomes of a penetration test?
There are both short- and long-term outcomes from a penetration test – some delivered by the testing provider and some that require action from the customer organisation and their team.
The report from the provider should help an organisation understand where security is failing to align with certain standards or business needs. Some of the insights and recommendations that may be provided include:
- A list of vulnerabilities, categorised by risk, impact, and severity, so adequate measures can be deployed to stop them.
- An idea of how findings translate to business risk, so strategies can be developed to improve cyber resilience through cybersecurity measures.
- Threats that may already exist within an estate, and how to identify and eradicate them.
Long-term, organisations can manage these findings as part of vulnerability and risk management programs.
Point in time penetration testing vs continuous testing
Penetration testing is an essential part of any cybersecurity strategy, and increasingly so. The point in time insights it provides act as a snapshot of security at a specific juncture. In the post-digital era where new applications, systems, and infrastructures are perpetually implemented, engineered, and modified, this enables organisations to achieve a high bar in the shortest amount of time possible.
New testing approaches that address the need for continuity can help maintain that bar. These “continuous security testing” solutions provide asset identification and vulnerability analysis that’s always on. Rather than analysing specific, tactically scoped areas, they help to maintain security right across your estate, thus feeding into a vulnerability management strategy. Where penetration testing is suitable for testing within a limited context (one application within a specific domain, for example), continuous security testing is akin to having an automation toolbox and a team of security engineers looking for vulnerabilities and other weaknesses right across your organisation in a business context.
The importance of continuity
The rise in opportunistic scan and exploit attacks can be tied to the universal pace of change and growth across digital infrastructures. What your business deems important has only some bearing to what will be targeted because there is now so much on offer. Security budgets are not finite and in many cases are being constrained. Organisations are realising the importance of security culture within every department, especially (with the rise of DevSecOps) in their development and engineering teams. The playing field has moved.
Continuous testing helps tackle this shift in the following ways:
| Business challenge | Provision of continuous security testing |
| New vulnerabilities emerge daily, constantly adding risk to the business. | Continuously seek and identify, and recommend remediations for, new (known and unknown) vulnerabilities. |
| Potential for unknown risk because of limited security visibility. | Increase visibility of vulnerabilities and other weaknesses across the entire estate. |
| Limited budget and unfulfilled remediations leading to security debt. | Helps prioritise remediations according to likelihood of exploitation and impact. |
| New requirements to quantify operational resilience. | Reveals a dynamic view of the organisation’s security and how remediations are having an impact over time. |
| Create a business-wide security culture. | Analyse new parts of the estate, uncover shadow IT, and align security with development speed. |
To find out more about continuous security testing, watch the recording of our recent webinar, Beating bad actors to find vulnerabilities in your systems.
Whilst continuous security testing is becoming more and more essential, it should not be seen as a replacement for penetration testing. Read our article on whether or not penetration testing can be automated to learn more.
How to improve your penetration testing strategy
This is both an exciting and challenging time for security teams. For every opportunity offered by this new area of technology, there are new threats to be faced, new budgetary limitations, new resource limitations, and so on. Good news: security testing is evolving too. Point-in-time penetration should remain a key activity within all organisations’ cybersecurity programmes, but now is the time to consider how continuous activities can be overlaid to provide the necessary level of visibility and control across your estate.
To find out more, explore our penetration testing and continuous security testing services.

Related articles

Reports of Scattered Spider attacks on US insurance firms

Compromising email logins and backup keys from online error messages

How to get the most out of a penetration test scoping exercise

How many disguises would you pack to break into a data centre?

How to create a bespoke risk-based testing strategy
