Getting a handle on your growing application estate
According to research by IT service management company Okta, in 2019, their customers were deploying an average of 88 applications, a 6 per cent increase on 2018 figures, with 10 per cent of its customers deploying 200 apps or more.
Research by McAfee confirms this, with the security firm finding that companies with 50,000 employees or more now operate 788 custom applications on average. In fact, on average, the number of new applications enterprises will develop in the next 12 months is expected to reach 37 per organisation. While this application explosion is a key part of many organisations’ digital transformation journeys, securing an ever-growing application estate is a task that IT teams are grappling with. Faced with the challenge of keeping up with the speed of DevOps, while also ensuring that security remains water-tight, many organisations are now asking whether a new approach to security testing is needed.
Under pressure
As the often quoted phrase goes, every company is a software company today. Under increasing pressure to digitise at speed, having effective software solutions deployed across all aspects of operations is now an essential part of how businesses deal with customers, suppliers, and employees across numerous industries.
This has only increased as a result of the Covid-19 pandemic, with a shift to remote working and the need to reach customers in new and innovative ways, further accelerating the trend.
Aided by DevOps and Agile approaches, which aim to shorten the development cycle of new applications and updates to existing software, organisations are now able to develop and deploy applications for a whole host of purposes.
While this may be beneficial for business, security teams are struggling to keep up.
An attractive target for hackers
That’s because the number of applications that the average security team needs to monitor, patch, and protect has grown exponentially in recent years.
As web-based applications are now a key part of how numerous organisations operate, they have inevitably become a prime target for cyber criminals.

Fig. 1 : Data breaches analysed this past year that were the result of a web application vulnerability
Some applications may be developed in-house, some by third-party developers, and many will be based around off-the-shelf commercial software. But they all offer an attack surface for cyber criminals, especially if there are coding errors, deployment misconfigurations, or issues with the infrastructure they run on.
As a result, attacks targeting web application are on the rise. According to research by CDNetworks, in the first half of 2020, attacks against web applications rose by more than 800 per cent compared with the first half of 2019. Verizon estimates that 43 per cent of breaches targeted web applications over the last 12 months, more than double the number from the previous year.
In a recent survey conducted by Computing, 60 per cent of contributors agreed that the frequency of cyberattacks against applications is increasing, with 71 per cent agreeing that attackers are employing more advanced techniques.
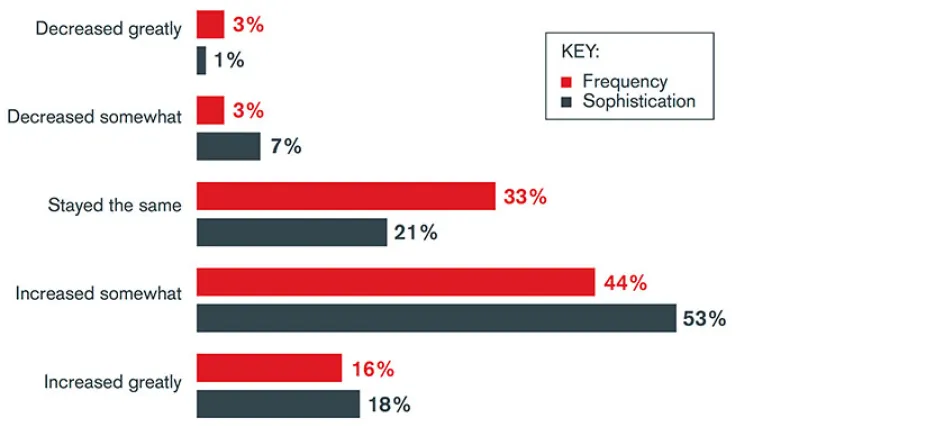
Fig. 2 : How has the frequency/sophistication of cyber-attacks against your organisation’s applications changed in the last two years?
Adversaries use attacks such as cross site scripting attacks, injection attacks and zero-day attacks to exploit web applications, typically targeting personal, financial and business data.
Furthermore, web attacks are becoming more advanced, with automated attack tools making it easier for networks of attackers to deliver attacks. According to CDNetworks’s State of the Web Security report, covering H1 of 2020, e-commerce, online learning, telecommuting and gaming were particularly targeted.
The impact of a successful attack can be serious. Applications provide adversaries with multiple entry-points into entire IT systems, exposing sensitive data and risking reputational damage.
A number of high-profile examples are testament to this. In 2020, British Airways was fined £20m by the UK Information Commissioner’s Office for a 2018 cyber-attack. Earlier this year, the personal data of 533 million users was posted online following a data leak.
Keeping on top of application security, and avoiding situations like this, is therefore paramount for any organisation. Part of this is testing applications for vulnerabilities that could act as a backdoor for hackers to get in. And with businesses developing their own applications or deploying those built by third parties at a rapid pace, ensuring security testing can keep up is a key concern.
In other words, can the average security testing strategy handle today’s application explosion?
The pen testing problem
In this context, cybersecurity professionals have had to rethink how they approach penetration testing and have deployed a number of tools and techniques to bring security checks closer to the speed that the developers need to release new features.
While penetration testing has been a key part of security strategies for some time now, complex applications require skilled and experience penetration testers for thorough examinations, making it impractical for many organisations, especially those lacking a substantial security budget, or those with hundreds of applications.
A typical application pen test can take anything from 3-15 days.How is an organisation with multiple digital assets, that are under continuous improvement, supposed to afford and schedule the penetration testing activities…even once a year? A question made even harder to answer when factoring in the resource and time needed to affect the recommendations received in the final analysis!
Employing the necessary cybersecurity professionals to carry out this task has also proved challenging. There is currently a significant cyber skills gap, with a 2018 study by the International Information System Security Certification Consortium finding that an additional 2.93m cybersecurity professionals were required to meet global demand. It revealed that 59 per cent of organisations were at moderate or extreme risk due to a cybersecurity skills shortage.
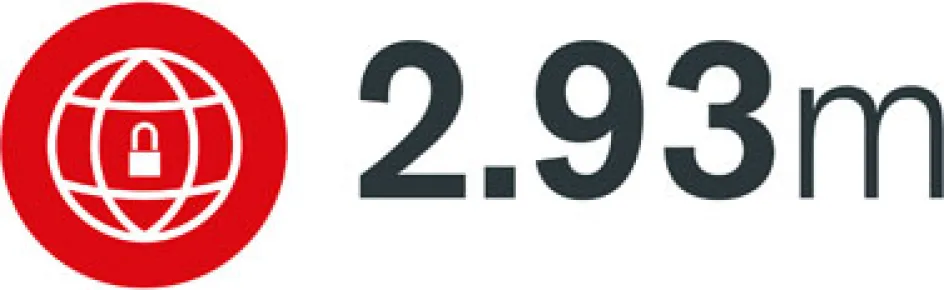
Fig. 3 : The number of additional cybersecurity professionals needed to meet global demand
According to the UK Department for Digital, Culture, Media and Sport, 48 per cent of businesses have reported a “basic skills gap” when it comes to cybersecurity, with 30 per cent reporting an “advanced skills gap”. Therefore, organisations often do not have the resources or the manpower to test each and every application within their ecosystem.
Application estate scanning
In order to address this issue, a number of application and infrastructure scanning tools have emerged. These allow organisations to scan the applications within their network for potential vulnerabilities. However, while they have their benefits, such as being able to be run regularly and over large estates, they have not proved as effective or comprehensive as human penetration testing.
As pen testing each individual application is unattainable for the majority of organisations, they are left with a choice over which applications to test in detail and which ones to scan. While organisations may opt to test only their business-critical applications, smaller apps can still provide a route for an attacker to infiltrate a system.
Automating some of these processes is an obvious solution to the issues outlined above. Although automation certainly has a role to play in application testing, automated scanning alone is unable to detect vulnerabilities with the same level of detail as human pen testers e.g. compromised business logic, session hijacking, and poorly configured authentication mechanisms (there are many others). Scanner outputs are undoubtedly useful and they should be part of every security strategy. They can be great indicators of problems that, when investigated by an experienced “white hat”, could highlight major weaknesses…often the scanner can understate the risk and the less experienced user not realise that a collection of seemingly unrelated low risk issues could be leveraged to execute a wholly more damaging attack. Put the scanner output in the hands of a professional and the value can increases dramatically.
A hybrid approach
It is clear that infrequent pen-testing routines cannot keep up with the frequency of change introduced by a DevOps team, over a large application estate, and tool-based scanning is not comprehensive enough on its own.
Therefore, it is clear that a new approach to testing, which accounts for the ever-increasing number of applications, the constant demand for newer and better features, and the shortages in cyber professionals, is needed. As a result, organisations must adopt testing strategies that involve a combination of manual pen testing and automated scanning but do it in a way that integrates and with development cycles and release schedules and delivers high quality results on a continuous and manageable program.
Combining skilled manual penetration testers, working as a team on an ongoing basis, with scanners tuned to cover web applications, has proven to offer a continuous testing plan of entire application estates that balances risk and affordability.
Continuous Security Testing
Multi-dimensional forces are at play that means ad-hoc penetration testing could be leaving organisations at unnecessary, or even unacceptable, risk. The previous discussion points cover the challenge in the business but what about external factors? Attackers toolsets are evolving all the time, shouldn’t we test when the threat changes? Third-party code is ubiquitous in most modern applications, if the third party code changes shouldn’t we test for new vulnerabilities.
The conclusion here is that in order to keep up with the pace of change, coming from all angles, security testing needs to operate on a continuous basis. Ad-hoc penetration testing should still feature but to get real impact on risk mitigation at the pace that your development team are writing code and at captures the random nature of new threats appearing, a systematic approach to deploying automated scanners and manual penetration testing is needed.
Continuous Security Testing addresses the choice between infrequent deep dives into individual applications or frequent, but less detailed, scanning that many organisations face by providing a continuous cycle of testing and remediation. In other words, the approach is able to keep pace with the rapid pace of application deployment without compromising on security.
This type of testing also represents a new and more blended way of managing application security. For many organisations, it also enables security teams to work more effectively and efficiently, and in tandem, with their colleagues responsible for DevOps.
In doing so, it gives organisations the tools to keep pace with the rapid development of new applications, ensuring security is at the heart of deployment, and large application estates can be managed effectively.
Related articles

Reports of Scattered Spider attacks on US insurance firms

Compromising email logins and backup keys from online error messages

How to get the most out of a penetration test scoping exercise

How many disguises would you pack to break into a data centre?

How to create a bespoke risk-based testing strategy