Cyber Essentials Update v3.1 Montpellier
Revisions to the Cyber Essentials scheme aims to align it with current technology advances and contemporary security risks. These updates help organisations enhance their cybersecurity measures and mitigate low-skilled cyber-attacks.
Cyber Essentials: Requirements for IT Infrastructure
These are the changes straight from the official Cyber Essentials documentation:
- The definition of ‘software’ is updated to clarify where firmware is in scope
- A statement on why asset management is important in Cyber Essentials
- A link to the NCSC’s BYOD guidance is added for information
- Clarification on including third party devices
- The ‘Device unlocking’ section is updated to reflect that some configuration can’t be altered because of vendor restrictions
- The ‘Malware protection’ section is updated
- New information about how using a zero trust architecture affects Cyber Essential
The definition of ‘software’ is updated to clarify where firmware is in scope:
This a change to the software definition that can be found on page 3 section B of the Requirements for IT infrastructure document, the software definition now includes “network software and firewall and router firmware”. This isn’t a vast change to the previous requirements as it’s always been a requirement to ensure firewall and router firmware is running the latest security updates that have been available for over 14-days and this remains the same, this update however has made this requirement easier to understand.
A statement on why asset management is important in Cyber Essentials
This is additional information provided by the NCSC around the importance of Asset Management and how it directly links into the controls for Cyber Essentials, the update can be found on page 4 within section C of the Requirements for IT Infrastructure document. Although this doesn’t affect the requirements, it’s always appreciated when additional guidance is provided to applicants that can help support their assessment and provide guidance on industry best practices and they are totally right, effective asset management can provide organisations the ability to make crucial changes to their IT assets and usually means less to no effect on day-to-day operations, this is important when applying for Cyber Essentials as applicants may be required to change the configuration of their IT assets to meet the standard for compliance.
A link to the NCSC’s BYOD guidance is added for information
This addition can be found on page 5 section (i) of the Requirements for IT Infrastructure document. It’s no bet that by now you know personal devices are included within your scope for Cyber Essentials if they are being used to access organisational data or services such as email, this includes both computing devices such as laptops and desktops and mobile devices. To achieve Cyber Essentials status with these devices in-scope can be challenging and if left un-managed pose a huge security risk to your organisation. If you require BYOD to be in-scope The NCSC has now provided a link to further information on managing these devices: Bring your own device (BYOD) - NCSC.GOV.UK
Clarification on including third party devices
This addition can be found on page 7 section (vi) of the Requirements for IT Infrastructure document. This is a superb addition to the document as a question around what external devices should be included in your scope for Cyber Essentials is asked on a regular basis. Well now it’s clearly defined, and a new graphic has been included:
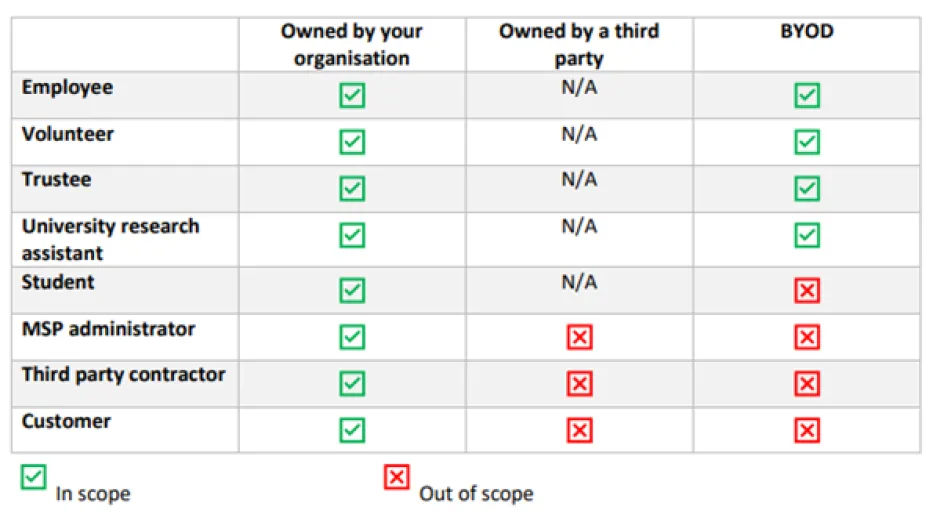
Where a device is defined as “out of scope” you are not required to implement the controls as these devices are usually not within your direct sphere of influence, however the user accounts they use on your systems are in-scope and must be configured in-line with the password-based requirements. This said these non-owned devices may pose a risk to your organisation if they are unsecure, when they connect to your systems they could already have malware on the device such as keyloggers and screen recorders due to unsecure anti-malware controls, asking your third-party to achieve their own Cyber Essentials to continue working with you will ensure there devices are close to the same security standard as yours, however this is not mandatory and is purely to lower the risk of a IT breach.
The ‘Device unlocking’ section is updated to reflect that some configuration can’t be altered because of vendor restrictions
This a change to ‘Device unlocking’ can be found on page 10 of the Requirements for IT infrastructure document. This is a welcome change as some mobile device vendors do not allow you to change the brute force mechanism on the device. Where you are unable to change these settings the scheme will now allow you to use the system default rate limiting or account lock settings for protecting the device. The pin number must still be in line with the requirements which is currently 6 digits in length and these requirements apply to devices where no username is required to authenticate into the device such as mobile phones and tablets.
The ‘Malware protection’ section is updated
This a change to Malware protection can be found on page 14 of the Requirements for IT infrastructure document. This is the biggest change to the requirements of Cyber Essentials but really doesn’t affect your assessment, it’s been updated to incorporate newer technologies for malware protection such as NGAV (Next Generation anti-virus) as many move from traditional signature based protection, the new requirements for devices that are protected by anti-malware software are:
If you use anti-malware software to protect your device it must be configured to:
- be updated in line with vendor recommendations
- prevent malware from running
- prevent the execution of malicious code
- prevent connections to malicious websites over the interne
These means that what ever anti malware software your organisation utilises, whether this be NGAV or traditional signature-based AV, the software, agent must be kept updated, prevent access to websites deemed as malicious, prevent the execution of malicious code that can reside within downloads etc and prevent malware from running on the system.
For devices that are protected by application whitelisting i.e. mobile devices, only approved applications, restricted by code signing, are allowed to be executed. You must:
- actively approve such applications before deploying them to devices
- maintain a current list of approved applications, users must not be able to install any application that is unsigned or has an invalid signature
No changes to application whitelisting and application sandboxing have been removed as a technical control for anti-malware.
New information about how using a zero-trust architecture affects Cyber Essentials
This addition can be found on page 14 of the Requirements for IT Infrastructure document. This additional information provides applying organisation that either have already adopted or are looking to adopt a Zero-trust architecture and highlights that implementing the Cyber Essentials controls do not prevent organisations from using zero-trust architecture as defined in the NCSC guidance: Zero trust architecture design principles - NCSC.GOV.UK
Cyber Essentials Plus: Illustrative Test Specification
These are the changes straight from the official Cyber Essentials documentation:
- Added all internally hosted servers to the Sample Testing section
- Updated the sub-test 2.1 criteria to CVSS base score of 7 or above
- Previous tests 4 & 5 removed and included in updated Test 3
- Malware Protection tests updated to align with changes to the technical requirements
Added all internally hosted servers to the Sample Testing section
This a change to the sampling section can be found on page 6 of the Illustrative Test Specification document. For Cyber Essentials Plus a representative sample of devices must be selected, these devices will be subject to various physical tests to confirm the controls are in place and working effectively, this update to sampling now includes internally hosted servers, this means that the servers you declare as in-scope during the self-assessment will now be subject to some of the same tests as an end user device.
A server is brought into the scope if it’s connected to the internet for any reason such as pulling updates or provides a service that exposed to the internet.
Internally hosted servers include any in-scope server that is hosted on the applying organisations local area network or within a datacentre or cloud environment where you can manage the patching of the server such as IaaS instances (Infrastructure as a Service).
These servers will now be subject to "Test Case 2: Authenticated Vulnerability Scan".
All other test cases only apply to EUDs and servers that allow a user to access a desktop environment and IaaS instances.
Servers that expose a service to the internet such as a web application (Http/Https) or file service (ftp/Sftp) for example will be scanned both authenticated and un-authenticated.
To sum up this change the servers in question will now be scanned for missing security updates in the operating system and applications that are installed on the server, any critical or high deemed over CvSS V3 score 7 or above where a patch has been available for more than 14-days will need remediating to achieve Cyber Essentials Plus status.
This a welcome change to the scheme and allows applying organisations that do not carry out regally vulnerability scanning to review their patching methods for servers during the assessment.
Updated the sub-test 2.1 criteria to CVSS base score of 7 or above
This a change to the Test Case 2 section can be found on page 6 of the Illustrative Test Specification document. A minor change but ad’s clarification for assessors to use the correct CvSS v3 metrics when assessing the vulnerability assessment results, the metric to use has always been the Base score and this is now defined in the documentation for Cyber Essentials Plus.
Previous tests 4 & 5 removed and included in updated Test 3
This a change to the Test Case 3 section can be found on page 7 of the Illustrative Test Specification document. Test Case 4: Check effectiveness of defences against malware delivered by email and Test Case 5: Check defences against malware delivered through a website have now been merged in to Test case 3: Check Malware Protection and are now sub-tests to this test case.
Malware Protection tests updated to align with changes to the technical requirements
For organisations using Next generation Anti-malware controls the assessor may be required to carry out further checks if the test files were not used to prove that the software was installed and operational. Sub-test 3.1.4 that can be found on page 8 of the Illustrative Test Specification document now states the following:
The following manual checks must take place on all sampled EUD, servers that provide a user-interactive desktop and IaaS instances that use anti-malware software and the tests files were not used to prove that the software was installed and operational:
- the anti-malware software is installed and operational through investigation of logs
- and the anti-malware software is updated in accordance with the vendors configuration instructions
If the assessor can evidence that the anti-malware software is installed and updated in accordance with the vendors instructions a pass can be awarded for this test.
To find out more about Cyber Essentials, the benefits, what the different levels of certification mean, and how you can become certified, click here.
Related articles

Reports of Scattered Spider attacks on US insurance firms

Compromising email logins and backup keys from online error messages

How to get the most out of a penetration test scoping exercise

How many disguises would you pack to break into a data centre?

How to create a bespoke risk-based testing strategy
